Explore global internet censorship with network testing

The internet is not the same everywhere. In some countries, you can visit most websites and services as you like, while in other countries, governments and internet providers control what you can see. This practice is called internet censorship, and it has a big impact on people’s lives, on how they use the web and what information they can access.
In this blog post, we will take a closer look at global internet censorship, how it works, and how you can use Globalping to check for censorship from virtually any location worldwide.
What is internet censorship?
Internet censorship means limiting or controlling what people can access online. Usually, governments are the ones enforcing it, but ISPs (internet service providers) and online platforms can also play a role. Often, the reasons and motivations behind internet censorship are political, wanting to limit certain kinds of speech. However, it can also be about security or protecting copyright.
Censorship typically follows these goals:
- Blocking access to websites or services, for example, a social media or news platform
- Blocking or filtering content by removing articles, videos, or even keywords without blocking the entire website
- Slowing down services so that users give up on using them
There are different methods to reach these goals:
- DNS blocking or tampering: prevents a domain from resolving to its correct IP address
- Content filtering and packet inspection: examines network traffic headers or other unencrypted fields and blocks connections that match defined patterns.
- Redirecting: sends users to different pages, for example, an unrelated site or a government page
- Man-in-the-middle (MITM) techniques: intercepts and decrypts traffic to see the entire content, allowing surveillance and content manipulation
- Traffic throttling: slows down connections to disrupt usage
These methods can be used on their own or in combination, and their usage often varies between countries.
How to detect internet censorship with Globalping
Globalping is a free network measurement platform powered by a vast network of community-hosted probes. This global network lets you test how websites and services behave from virtually any location.
We've built various tools to use Globalping, so you can choose what works best for you, including a CLI tool, a web tool, and apps for Slack and Discord, as well as an MCP server.
Before we start testing, here are some limitations to consider:
- A failed test doesn't always mean there is censorship; there could also be a firewall or a misconfigured server.
- The results can change depending on the provider the probe is connected to.
- You need context to understand the results. For example, you should know how a site usually responds.
In our examples below, we'll use the Globalping CLI tool, but you can run these tests with any other official Globalping integration as well. If you don't have any Globalping tool set up yet, we recommend using our website tool, which requires no installation or setup on your end.
Basic reachability
Using ping, we can test whether a site is reachable from specific locations.
Example:
globalping ping example.com from china
If probes in one country can't reach the target while probes in other countries can, this may indicate a block.
DNS tampering or blocking
DNS (Domain Name System) converts a domain name into the IP address needed to visit a webpage. If censored, you may receive wrong, empty, or misleading results/IP addresses.
Example:
globalping dns example.com from iran
Make sure to compare the IP addresses you get from testing in different countries: If one location returns no result, or the wrong IP, that's likely DNS manipulation.
Blocked content, redirects, and altered responses
Even if a website seems to load normally, there may be content missing, changed, or replaced. You might also get redirected to a government warning page or an unrelated site. By running HTTP requests with Globalping, you can find out more about the content served in specific locations.
Example:
# http head
globalping http https://example.com --from russia
# http get
globalping http https://example.com --from russia --method get
- HTTP HEAD shows response headers, status codes, and redirect information without downloading the content
- HTTP GET returns the complete HTML that users in that location actually receive
In the results, look for:
- redirects to other pages (government pages, unrelated pages)
- shorter, changed, or removed text/content compared to other countries
- response codes like 403 Forbidden or 451 Unavailable for Legal Reasons
Where do blocks happen?
Traceroute lets you see the path data takes across the internet, which makes it great for finding where and how censorship happens in the network infrastructure. For example, it helps you see if a block happens at the ISP, national internet gateways, or international internet exchange points (peering points).
Example:
globalping traceroute example.com --from turkey
What to look for in traceroute results:
- If the path ends before reaching its destination, packets may get blocked somewhere.
- Traffic that gets routed through unexpected locations or stays within the country instead of going to its actual destination.
- Asterisks or consistent timeouts may indicate where packets are dropped or filtered in the network.
Cross-check with multiple probes
To learn more, test from multiple probes in the same location using the limit option:
globalping ping example.com --from russia --limit 5
Then compare the results to see if all probes fail or only some. For example, this can help you find out if internet censorship is implemented by ISPs.
Example walkthrough
Let's go through an actual example. Let’s say we want to check if Facebook is accessible in Iran:
Ping test
Check if Facebook is reachable from different locations in the country.
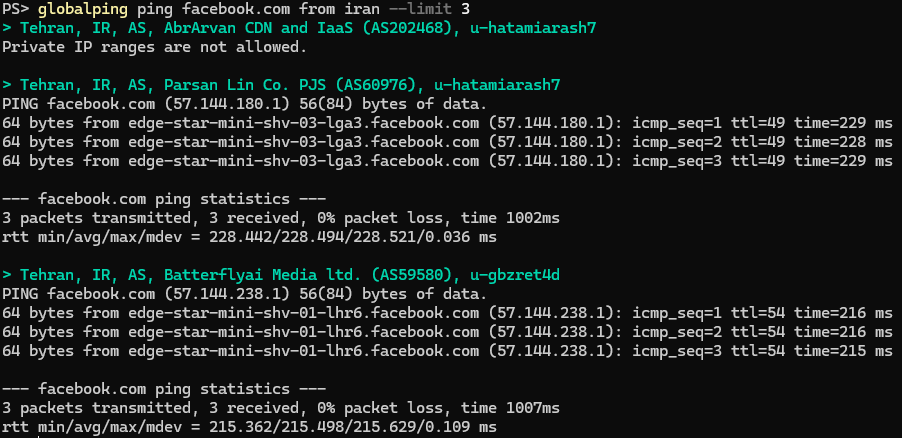
The ping results show mixed results from Iranian ISPs: one provider (AbrArvan) seems to return a wrong IP address that our tool can't even attempt to ping, while two other ISPs (Parsan Lin and Batterflyai) seemingly allow us to connect to Facebook servers (though a bit slow).
DNS test
See if the domain points to the correct IP address.
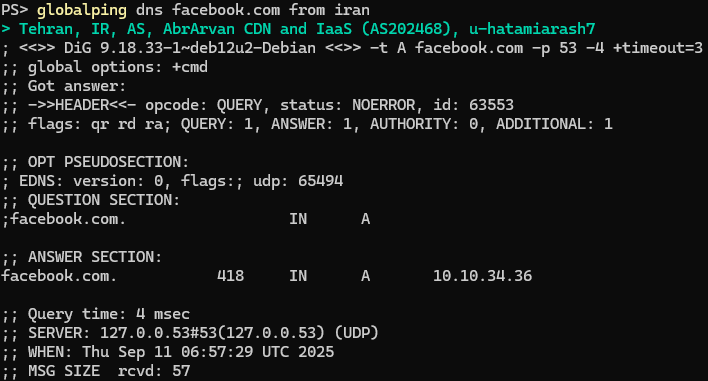
The DNS lookup from the AbrArvan ISP in Iran shows clear DNS tampering: instead of returning Facebook's IP address, it redirects facebook.com to a private IP address (10.10.34.36). As a result, users on that ISP can’t reach the real Facebook servers.
Let's focus on running tests on probes in ISP AS60976, from where we got a successful ping result.
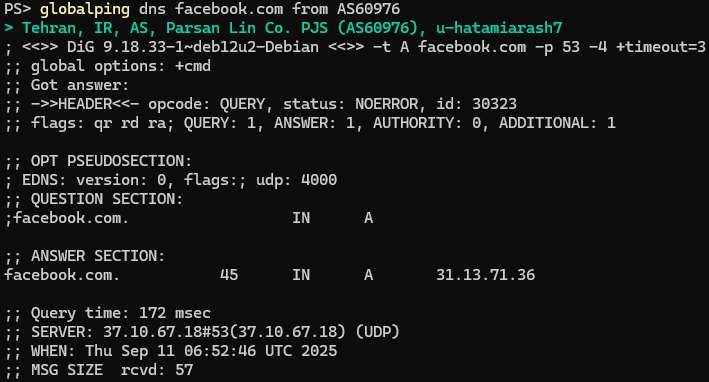
Running the same test from ISP AS60976 in Iran shows no sign of DNS tampering. Note again that, like in our ping test, the latency is a bit high, which can be worth keeping in mind during our investigation.
All in all, this is a good example of how different ISPs in the same country can enforce censorship differently.
HTTP test
Look at the headers to find redirects and see if the content matches other countries.
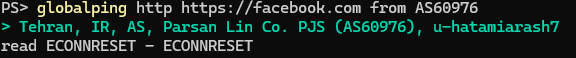
While the DNS lookup from the ISP AS60976 looked alright, we don’t get results from the HTTP HEAD request. This could mean that the ISP stops connections that try to access the site, i.e., users on that ISP also can’t access Facebook.
Traceroute
Track where the traffic goes and see if it's blocked or rerouted.
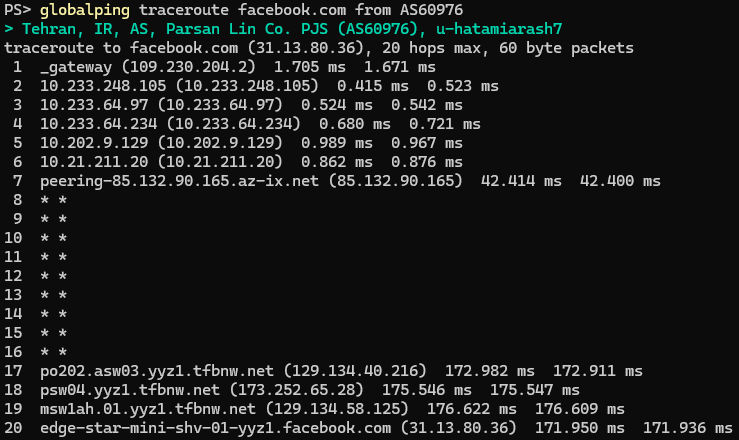
In this traceroute, we can see that the ISP is not blocking packets, and they even reach an international peering point (hop 7). Then we can see a gap between hops 8-16, which is normal since many routers simply don't reply. At hop 17, the route reappears at Facebook's servers in Toronto. This shows that the route itself is open for ICMP packets.
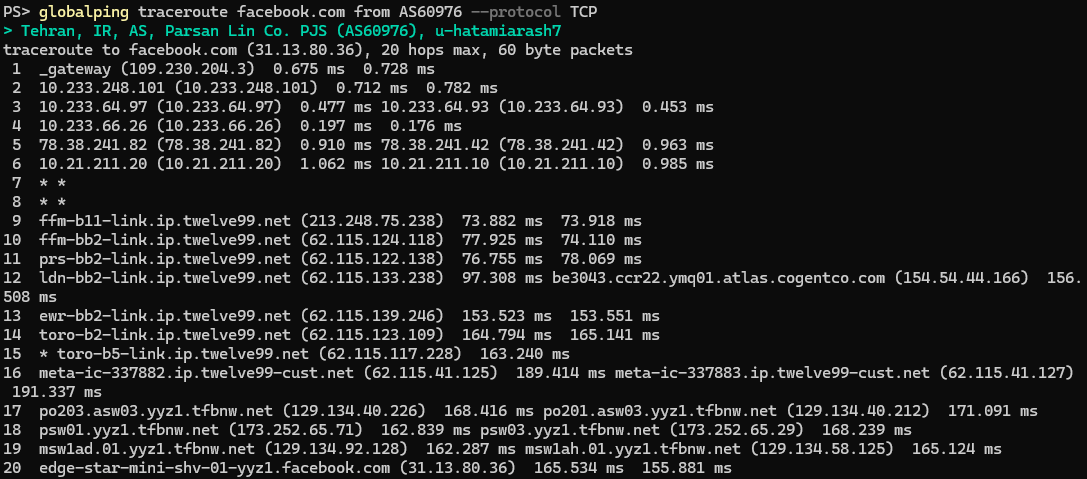
In this traceroute, we used TCP instead of ICMP to test whether the filter looks for a specific protocol. Again, the packets reached Facebook's servers, indicating that the route is open and that traffic leaves the country.
What does this mean for probes in ISP AS60976?
We know that when we try to load the website via HTTP, the connection gets terminated. However, the route is open when we run ping or traceroute. A possible explanation could be that the network lets through basic traffic but not web traffic to facebook.com.
In summary, during this experiment, we were not able to reach Facebook from our Globalping probes in Iran.
Conclusion
Internet censorship can be as obvious as blocking an entire service or as subtle as replacing some words on a website. By running simple network tests, you can explore how global internet censorship works and learn how users in different parts of the world experience the internet.
Ready to explore internet censorship yourself? Start running network tests with our website tool or use one of our many integrations for free.